Security Audit Procedures Security audits act as your business safety net to prevent information breaches and the consequential financial and ethical costs When conducting a security audit a business can assess its activity identify security pain points and risks and take a proactive approach for enhanced security
A security audit systematically assesses an organization s information systems policies and procedures to detect vulnerabilities guarantee regulatory compliance and improve overall security posture thereby defending against potential threats and data breaches An IT security audit is a systematic check on the security procedures and infrastructure that relate to a company s IT assets The purpose of the audit is to uncover systems or procedures that create security weaknesses
Security Audit Procedures

Security Audit Procedures
https://image2.slideserve.com/3759896/security-audit-procedures1-l.jpg

Security Audit Checklist 2024 Essential Tips And Tricks
https://cyberpandit.org/wp-content/uploads/2023/09/security-audit-checklist.webp

SCAN Audit Checklist PDF Download Part 2
https://compliancebangladesh.com/wp-content/uploads/2022/08/SCAN-Audit-Document-Checklist-1280x640.jpg
With the right approach your organization can achieve a steady cadence of auditing and maintain the visibility required to identify cybersecurity threats before they turn into data breaches Read on to learn how to conduct an effective cybersecurity audit to A cyber security audit allows you to identify weak points in your network evaluate the effectiveness of your security controls and ensure compliance with industry standards and regulations
A security audit is a comprehensive assessment of an organization s security posture and IT infrastructure Conducting an IT security audit helps organizations find and assess the vulnerabilities existing within their IT networks connected devices and applications 1 Define the scope and objectives The first step in conducting a security audit is to define the scope and objectives of the audit This involves identifying the assets and processes that will be audited as well as the goals and objectives of the audit
More picture related to Security Audit Procedures
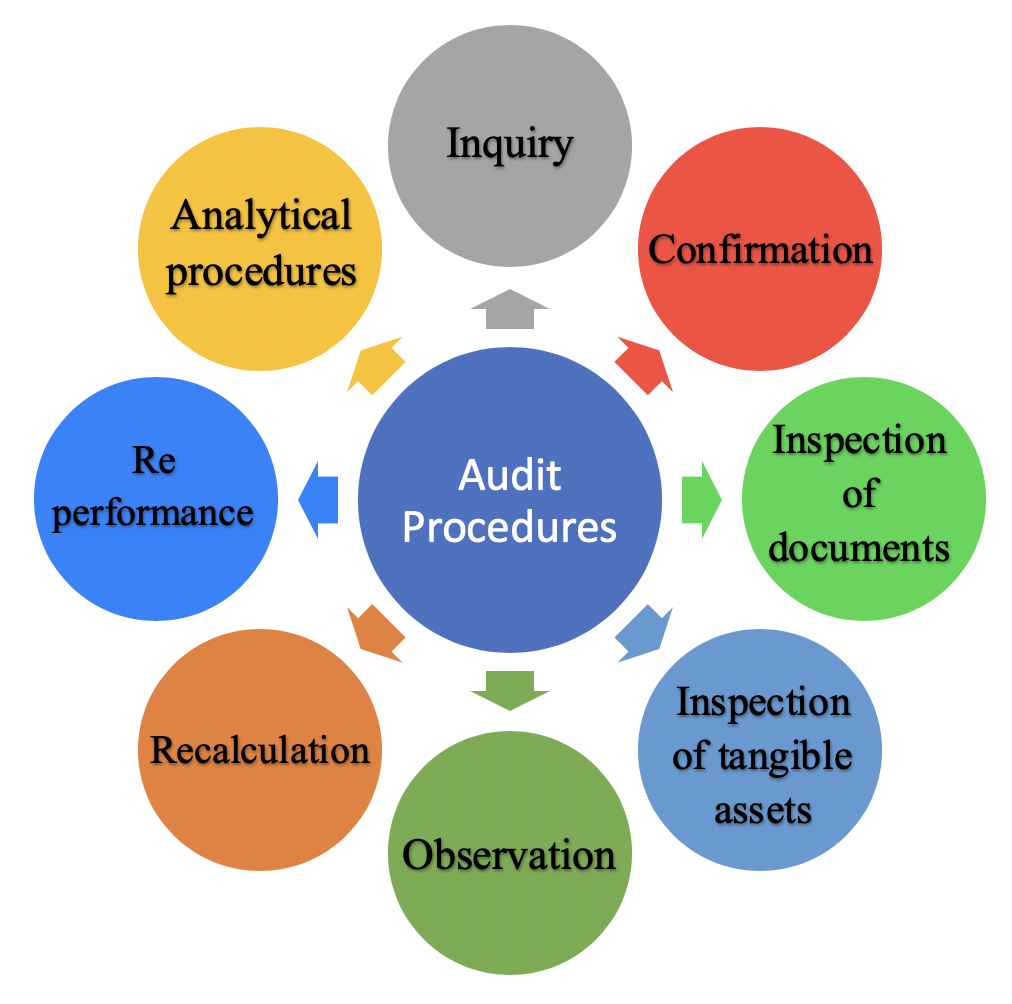
Audit Procedures Types Assertions Accountinguide
https://accountinguide.com/wp-content/uploads/2019/11/Types-of-audit-procedures.png

Comprehensive Cyber Security Audit Checklist For 2024
https://thecyphere.com/wp-content/uploads/2023/10/2-4.png
Cyber Security Audit Procedures Ppt Powerpoint Presentation
https://www.slideteam.net/media/catalog/product/cache/1280x720/c/y/cyber_security_audit_procedures_ppt_powerpoint_presentation_infographics_slides_cpb_slide01.jpg
In fact the cybersecurity audit universe includes all control sets management practices and governance risk and compliance GRC provisions in force at the enterprise level The essential aspects of any cybersecurity audit include the review of cybersecurity policies development of an integrated approach to cybersecurity analysis of the cybercompetence of personnel and the facilitation of risk based auditing initiatives in the organization Reviewing Cybersecurity Policies
[desc-10] [desc-11]
An Overview Of Audit Procedures And Techniques Vouching Audit Reports
https://imgv2-2-f.scribdassets.com/img/document/639135035/original/c8c9188f2f/1707692968?v=1

Performing A Security Audit Ignition
https://ignitionit.com/wp-content/uploads/2023/04/Security-audit-scaled.jpg

https://www.process.st/security-audit
Security audits act as your business safety net to prevent information breaches and the consequential financial and ethical costs When conducting a security audit a business can assess its activity identify security pain points and risks and take a proactive approach for enhanced security

https://qualysec.com/what-is-security-audit
A security audit systematically assesses an organization s information systems policies and procedures to detect vulnerabilities guarantee regulatory compliance and improve overall security posture thereby defending against potential threats and data breaches

Classification Of Audit CHAPTER CLASSIFICATION OF AUDIT 2 Complete

An Overview Of Audit Procedures And Techniques Vouching Audit Reports
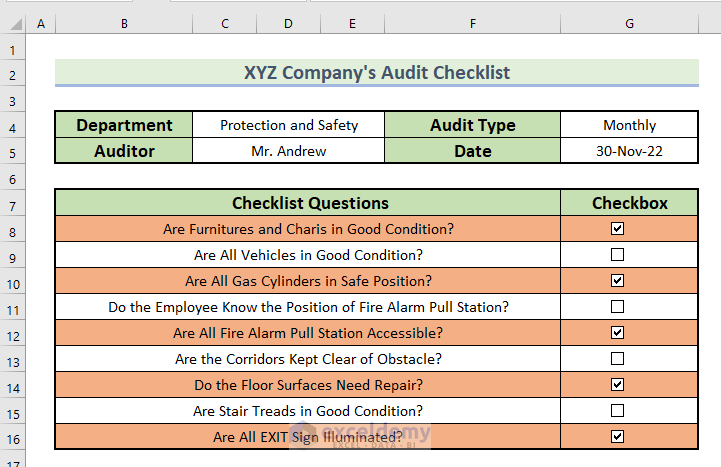
How To Create An Audit Checklist In Excel With Easy Steps
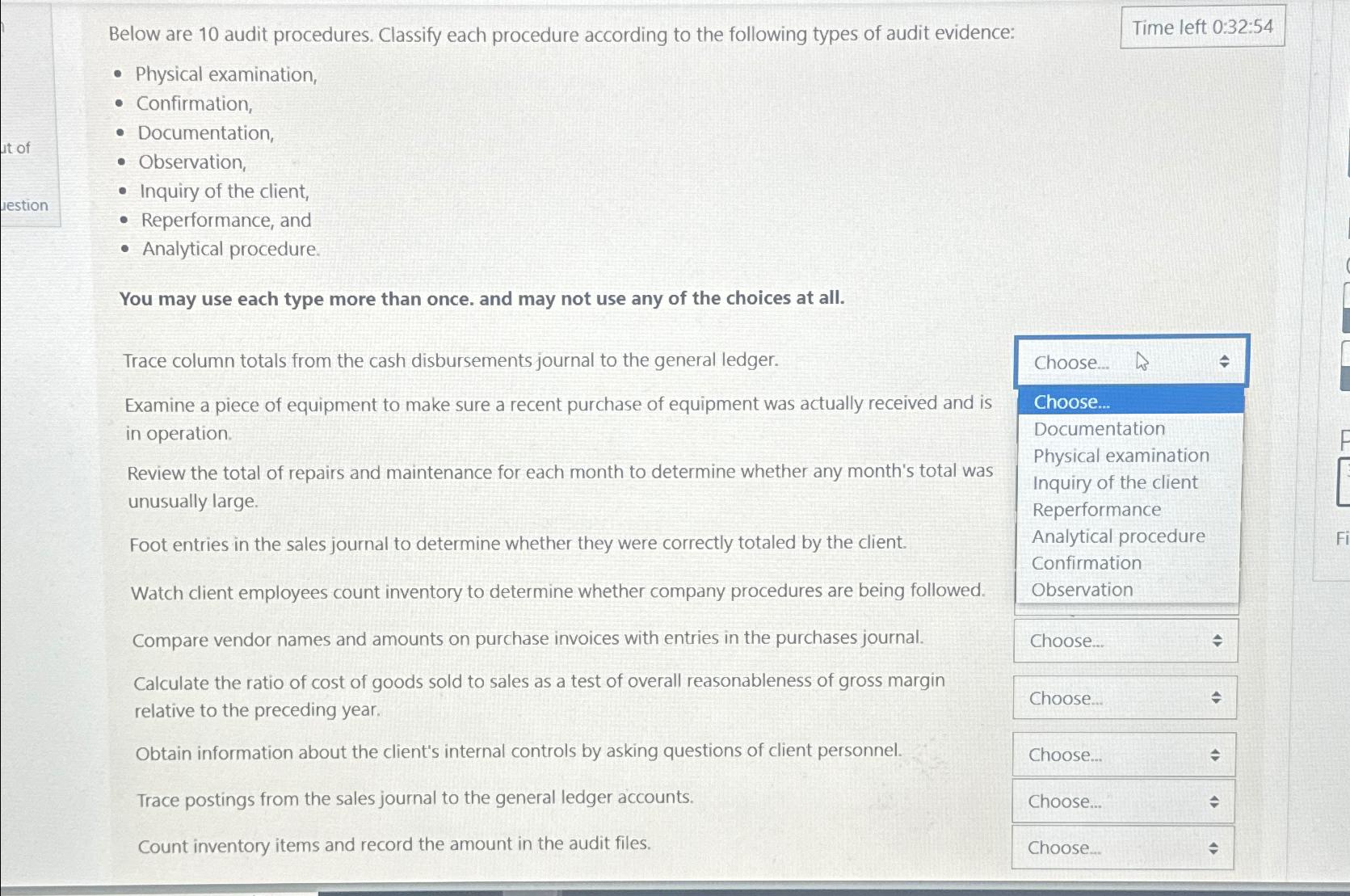
Solved Below Are 10 audit Procedures Classify Each Chegg

Exploring The Benefits Of Internal Audit Procedures

Explaining Audit Procedures

Explaining Audit Procedures
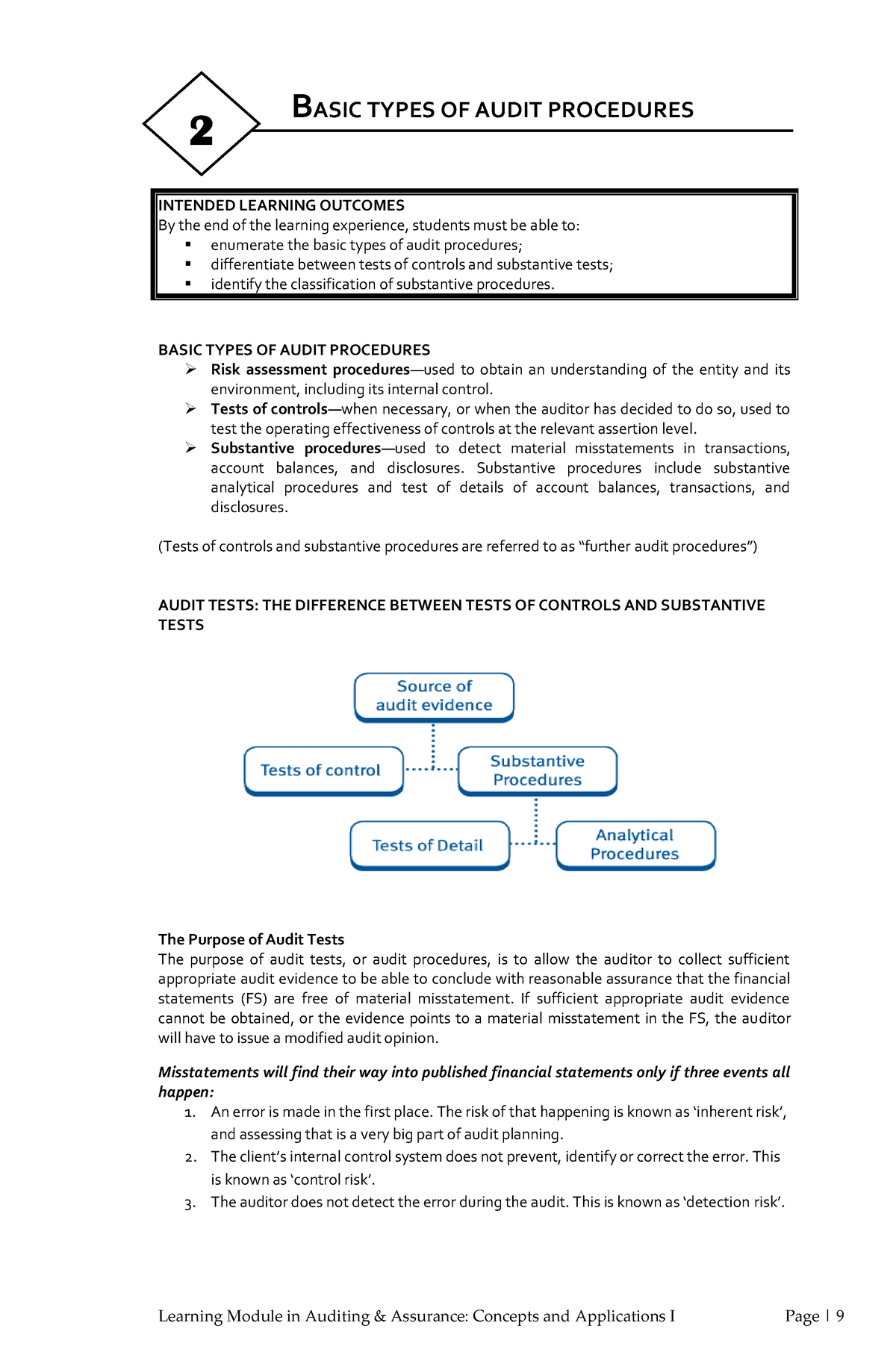
Basic Types Of Audit Procedure BASIC TYPES OF AUDIT PROCEDURES
.pdf/page1-1200px-Audit_Procedures_Checklist_-_8_31_2022_(1).pdf.jpg)
File Audit Procedures Checklist 8 31 2022 1 pdf AYSO Wiki

Redboard A Guide To Credit Union Audit Terminology
Security Audit Procedures - [desc-13]